If you are having a hard time accessing the Authentication And Its Types In Information Security page, Our website will help you. Find the right page for you to go to Authentication And Its Types In Information Security down below. Our website provides the right place for Authentication And Its Types In Information Security.

https://www.zhihu.com › question
Gemini API key Google API Key cursor google LLM gemini 2 0 flash thinking exp
https://www.zhihu.com › question
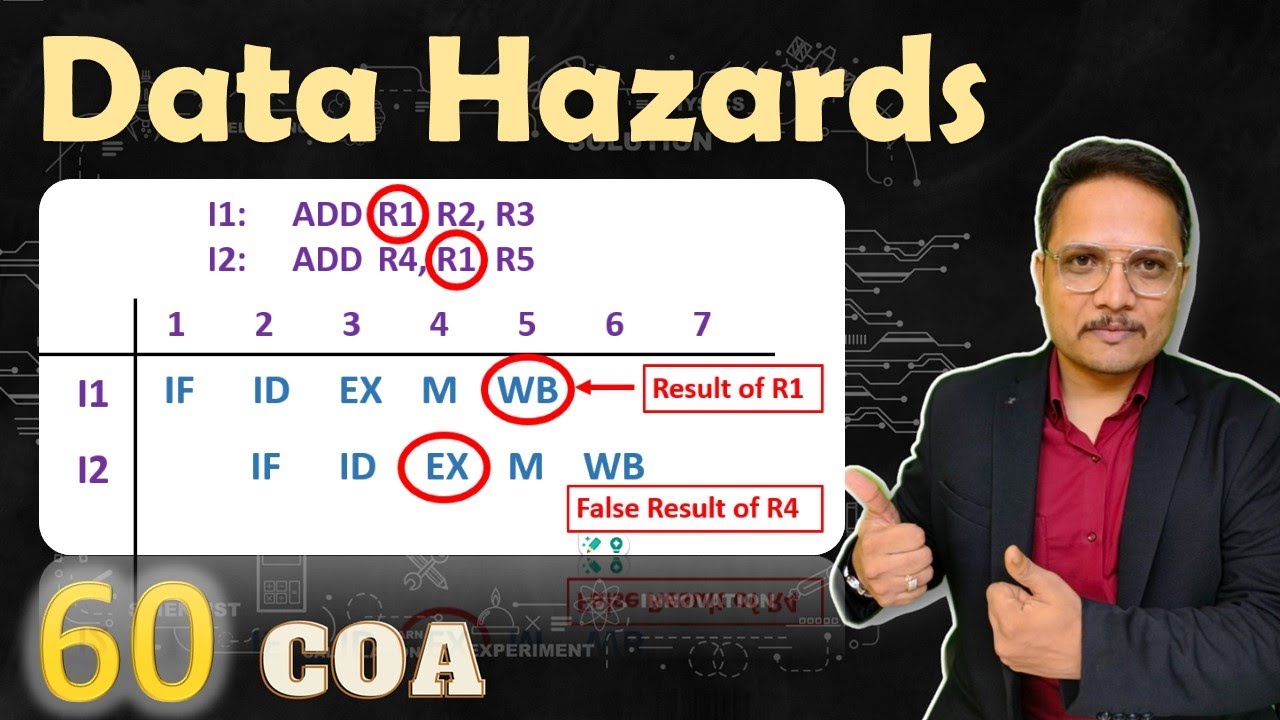
Git message authentication code incorrect



https://english.stackexchange.com › questions
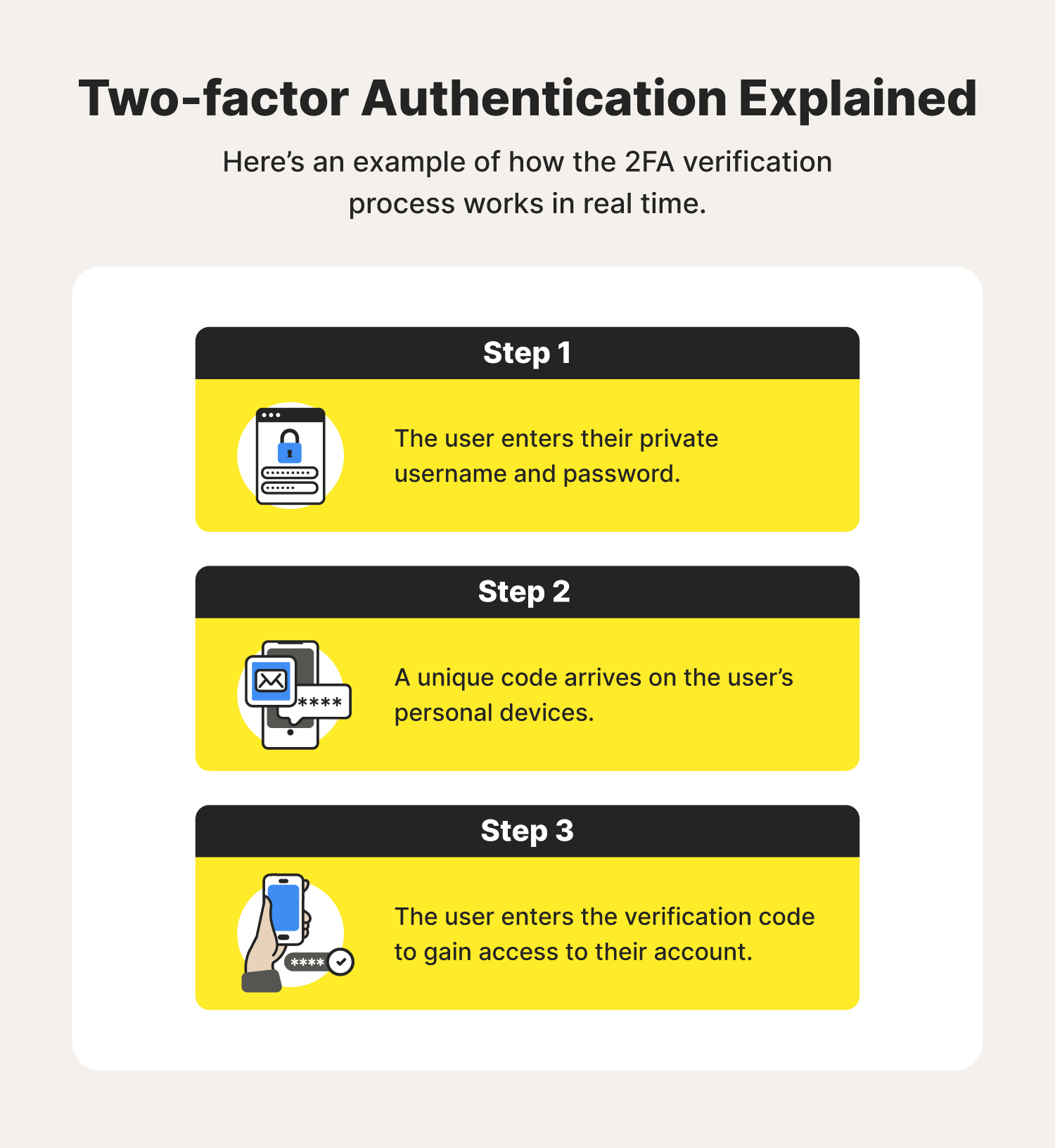
My professor used the word authentification in a lecture I have always used authentication Is it a real word or is authentication the correct term

https://www.zhihu.com › question
Linux Ubuntu QT Authentication failed ping 2
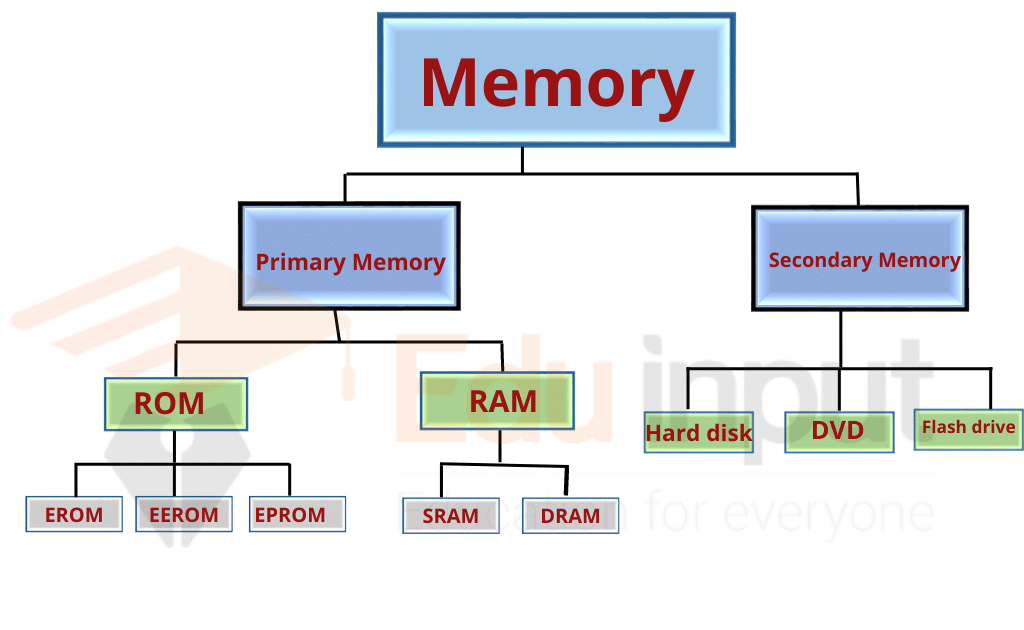
Thank you for visiting this page to find the login page of Authentication And Its Types In Information Security here. Hope you find what you are looking for!