If you are having a hard time accessing the Protocols For Secure Communication In Cryptography page, Our website will help you. Find the right page for you to go to Protocols For Secure Communication In Cryptography down below. Our website provides the right place for Protocols For Secure Communication In Cryptography.

https://www.comparitech.com/blog/information...
These algorithms and others are used in many of our secure protocols such as TLS SSL IPsec SSH and PGP In this article we will discuss what encryption actually is what it does some of the key concepts behind it We will give you an introduction to these major types of encryption and the secure protocols that use them What is

https://assets.cambridge.org/97811070/14275/front...
The relevant algorithms protocols and techniques this i nsightful introduction to the foundations of modern cryptography is ideal for graduate stu dents and researchers in engineering and computer science and practitioners invol ved in the design of security systems for communications networks Richard E Blahut
https://www.researchgate.net/publication/372339428...
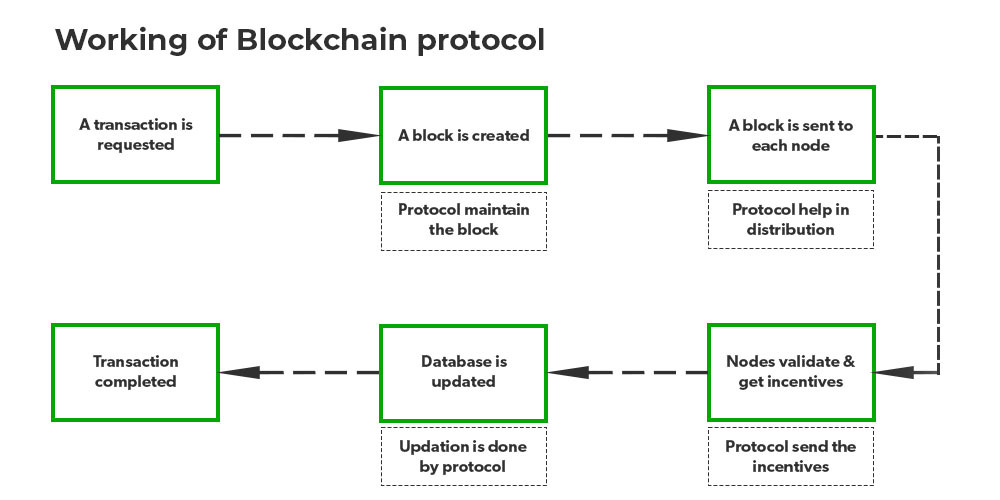
This abstract examines the evolution of secure communication protocols and data protection techniques as it relates to the advancements in cryptography The development of post quantum

https://thecryption.com/blockchain/the-basics-of...
Cryptography is the science of secure communication It is used to encrypt sensitive data and provide authentication and non repudiation services

https://www.cambridge.org/core/books/cryptography...
A security protocol consists of a formal method of using a cryptographic technique in a practical application Without a well defined security protocol a perfectly secure cryptographic technique could be compromised by its use

https://www.cs.utexas.edu/users/misra/Classes.dir/...
Be transmitted rst in a secure manner a problem known as key exchange For these and other reasons this form of encryption is rarely used in high security applications A major problem in devising a secure communication protocol is that Alice may send several messages to Bob and as the number of transmissions increase

https://www.cloudflare.com/learning/ssl/transport-layer-security-tls
Transport Layer Security or TLS is a widely adopted security protocol designed to facilitate privacy and data security for communications over the Internet A primary use case of TLS is encrypting the communication between web applications and servers such as web browsers loading a website
https://www.iso.org/information-security/what-is-cryptography
Quantum cryptography is a method of encryption that applies the principles of quantum mechanics to provide secure communication It uses quantum entanglement to generate a secret key to encrypt a message in two separate places making it almost impossible for an eavesdropper to intercept without altering its contents
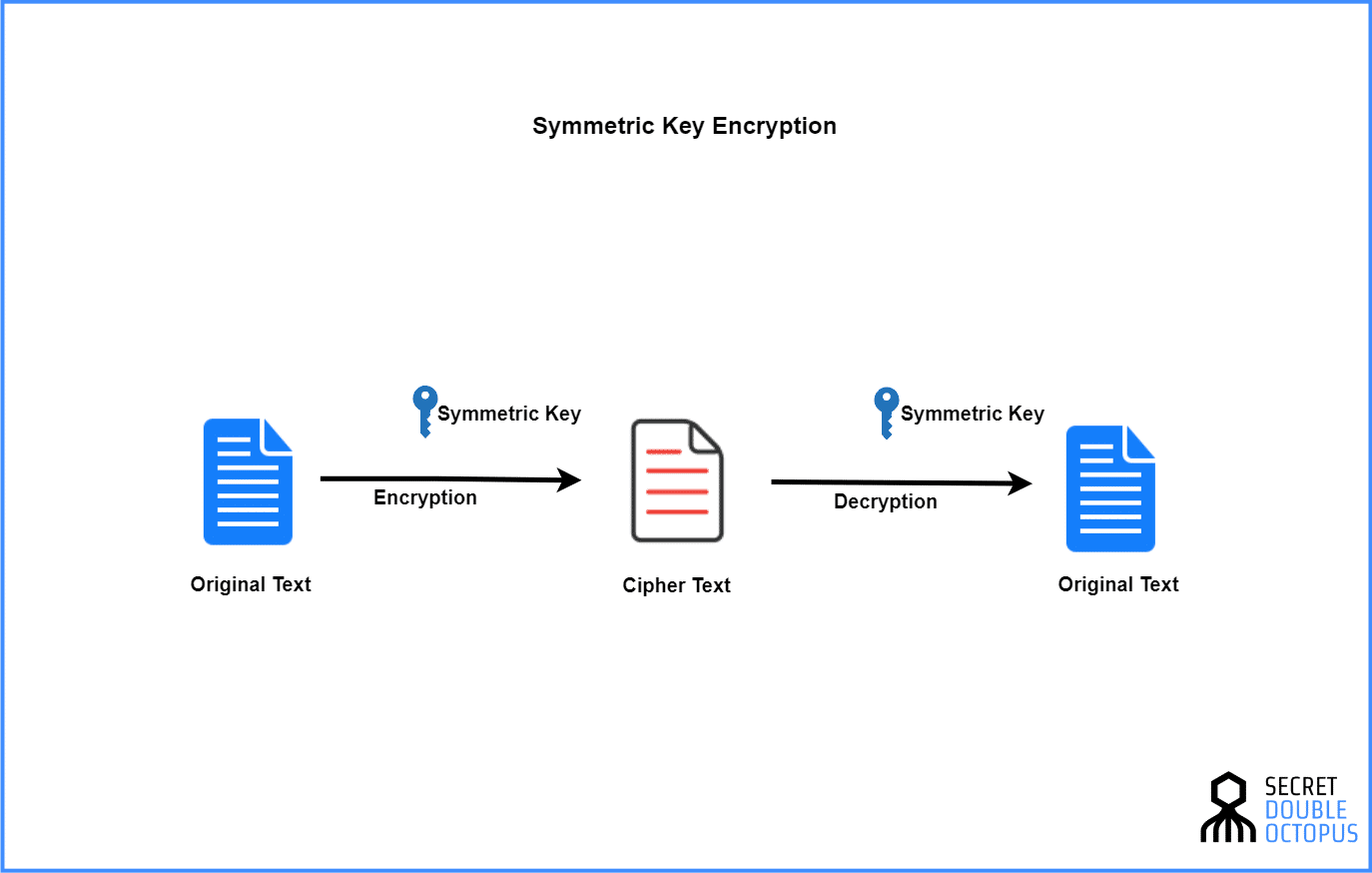
https://www.cambridge.org/core/books/cryptography...
The nature of social and economic interaction can impose a great variety of subtle requirements on the structure of a communication system to ensure various forms of security privacy and trustworthiness Secrecy and authentication are complementary functions in a communication system
Thank you for visiting this page to find the login page of Protocols For Secure Communication In Cryptography here. Hope you find what you are looking for!