If you are having a hard time accessing the Hmac Authentication Rest Api Example Java page, Our website will help you. Find the right page for you to go to Hmac Authentication Rest Api Example Java down below. Our website provides the right place for Hmac Authentication Rest Api Example Java.

https://security.stackexchange.com › questions
Yes because a HMAC can do everything a regular hash function can do However a HMAC can aside from integrity also guarantee authenticity assuming that the key has not been

https://crypto.stackexchange.com › questions
Note that HMAC is a specific scheme as Seth correctly describes SHA 3 uses KMAC which is therefore another hash based MAC Maybe the acronyms CBMAC and HBMAC could be used for Cipher

https://crypto.stackexchange.com › questions
I have three questions Would you use HMAC SHA1 or HMAC SHA256 for message authentication How much HMAC SHA256 is slower than HMAC SHA1 Are the security improvements of SHA256

https://crypto.stackexchange.com › questions
These are some examples HMAC SHA256 vs RSA SHA256 which one to use What are the different use cases between an HMAC and digital signature I am designing an SSO single

https://crypto.stackexchange.com › questions
SHA512 HMAC uses a bit key and produces a 512 bit digest But I am unable to find definitive key sizes for SHA224 SHA384 and SHA512 The HMAC RFC 2104 lists this We denote by B the byte

https://security.stackexchange.com › questions
Is there anything different about how secure these two hashing algorithms are Does HMAC fuse the data and the key in a special way that s more security aware
https://security.stackexchange.com › questions
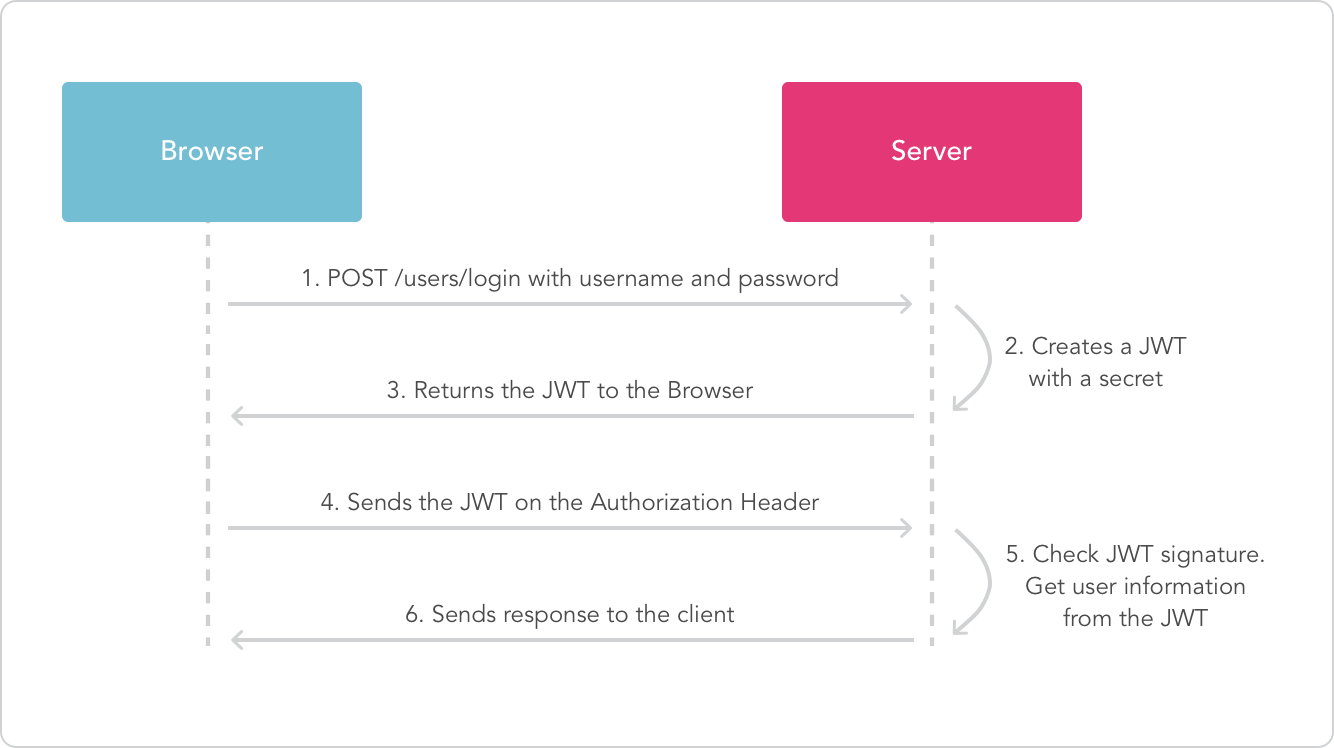
I m creating HTTP REST service which will be available over tls only For authentication purposes I plan to generate JWT token for every user using HMAC HS256 I need a secret key for

https://crypto.stackexchange.com › questions
That said the construct of HMAC SHA1 is still considered safe to use assuming a secret key due to the security proof for HMAC which does not rely on collision resistance of the underlying PRF
https://crypto.stackexchange.com › questions
PBKDF2 uses a pseudorandom function for example HMAC SHA256 What I understand is that PBKDF2 uses HMAC SHA256 for c iterations Why not just use HMAC SHA256 directly I
Thank you for visiting this page to find the login page of Hmac Authentication Rest Api Example Java here. Hope you find what you are looking for!