If you are having a hard time accessing the Graph Authentication Methods page, Our website will help you. Find the right page for you to go to Graph Authentication Methods down below. Our website provides the right place for Graph Authentication Methods.
https://www.zhihu.com › question
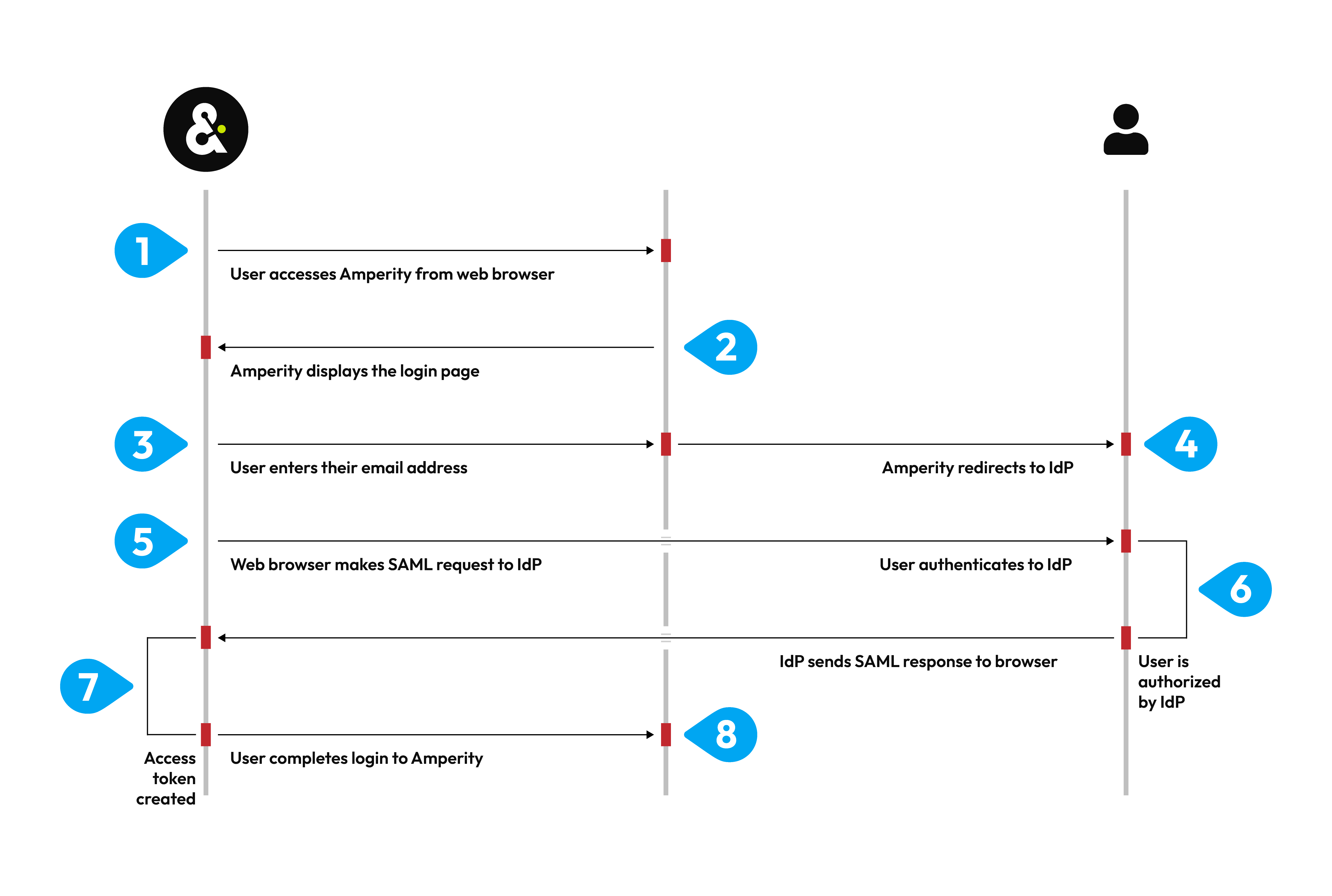
Graph chart diagram form table Graph graph paper Chart


https://www.zhihu.com › question
Graph Agent Framework API Augmented LLM Spring AI

https://www.zhihu.com › question
VLLM prefill CUDA Graph prefill batching CUDA

https://www.zhihu.com › question
Spectral graph theory spectral graph theory 4 GCN Graph Fourier Transformation Graph Convolution

https://www.zhihu.com › tardis › zm › art
SFC Sequential Function Chart IEC 61131 3 PLC
https://www.zhihu.com › question
Graph GraphQL API SQL Structured Query Language
?w=186)
https://www.zhihu.com › question
Vllm cuda graph cuda gragh gpu cpu gpu

Thank you for visiting this page to find the login page of Graph Authentication Methods here. Hope you find what you are looking for!